Service and product according to all stages of your IT security needs.
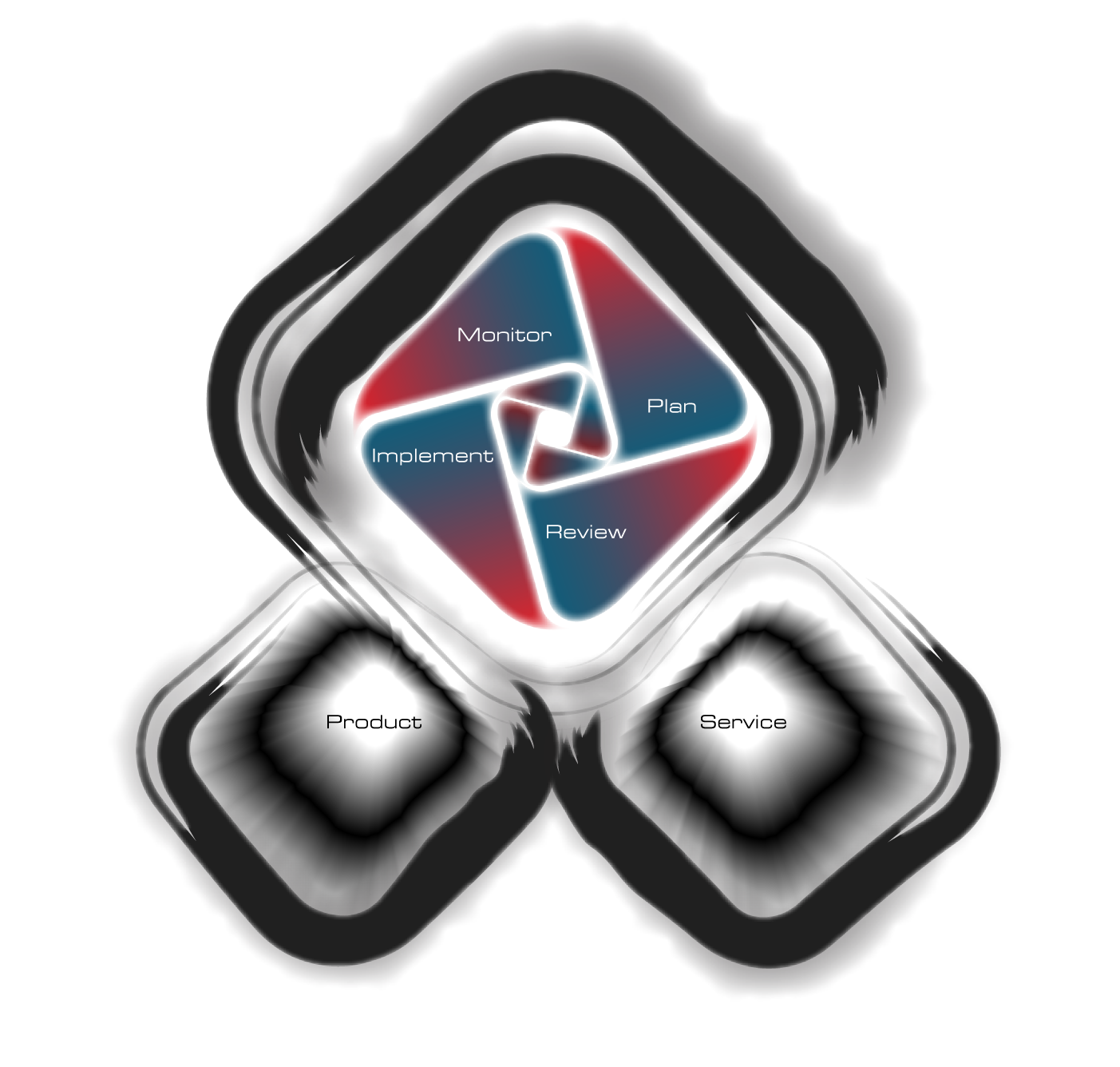
As different services and products are needed in different occasions, we formulated our solution into 4 interrelated stages: Plan, Review, Implementand Monitor
Services
Products
All stages are equally important to the security systems which are worth tackling one by one.
Plan
 Our consultants provide advices on the latest IT security trends. Besides consulting service, our consultants also help the clients to design and develop security plans and infrastructure designs in accordance to clients’ business requirements. IT Documentations could also be reviewed and assessed. Our experienced consultants could also conduct trainings to bring in new technologies and knowledge to clients.
Our consultants provide advices on the latest IT security trends. Besides consulting service, our consultants also help the clients to design and develop security plans and infrastructure designs in accordance to clients’ business requirements. IT Documentations could also be reviewed and assessed. Our experienced consultants could also conduct trainings to bring in new technologies and knowledge to clients.
Review
 IT Audit Service is used to review organizations IT readiness and compliance. Our consultants verify and conduct IT operation, development, design and compliance reviews on the client’s network systems using COBIT standard procedures. According to the standard provided by clients, Security Design would also be assessed. Penetration Test would also be conducted using non-intrusive penetration method .
IT Audit Service is used to review organizations IT readiness and compliance. Our consultants verify and conduct IT operation, development, design and compliance reviews on the client’s network systems using COBIT standard procedures. According to the standard provided by clients, Security Design would also be assessed. Penetration Test would also be conducted using non-intrusive penetration method .
Implement
 During IT Security assessment and audit services, threats and vulnerabilities would be identified. In order to ensure the systems are well protected against potential exploitations from internal and internet attacks, our consultants provide rectification support services for clients.
During IT Security assessment and audit services, threats and vulnerabilities would be identified. In order to ensure the systems are well protected against potential exploitations from internal and internet attacks, our consultants provide rectification support services for clients.
Monitor
 Our consultants analyze the adequacy of clients’ current IT protection mechanism and identify potential vulnerabilities and mechanism of attacks. Additional incident handling and emergency response support services and post incident handling services could also be provided. Even though security measures are implemented, there are still chances that the IT systems would be attacked. Our consultants provide advices and supports for our clients during security incidents.
Our consultants analyze the adequacy of clients’ current IT protection mechanism and identify potential vulnerabilities and mechanism of attacks. Additional incident handling and emergency response support services and post incident handling services could also be provided. Even though security measures are implemented, there are still chances that the IT systems would be attacked. Our consultants provide advices and supports for our clients during security incidents.
